Due to their alluring character, the porn websites have a magnetic effect upon people, these are the places where the people let the guard down easiest, clicking blindly on links and buttons, downloading, running, updating all what is requested or offered by these websites in an attempt to achieve more quickly their unique goal in that moment: to watch a porn video clip. It’s not a problem to view a porn video clip as far as the website visitor is +18 and the website is clean of malware, the problems starts to appear when the visitor is landing on a fake porn video website because on the other side of the barricade, the malicious persons being aware of the “temporary blindness” effect upon people, choose the fake porn web site as the best method to attract people in order to spread their malware, to infect computers and to build botnets of zombie computers. There are little variations of the method used to convince people to run the malware: it’s offered as an indispensable video codec, as a video player even with a well-known name like Adobe Flash Player or as an update of an important and much-needed browser plugin.
We can put on fake porn websites list this webpage:
http://fimoypocicar.homepc.it/land/video.php?l=4:50&id=1&n=my_loli2&a=elpilonnero&path=./tmb/my_loli2/01.jpg&rat=./img/rating5.jpg&v=54665

fake-porn-website
which in the moment when somebody click the Play button in the movie window, is offering a fake Adobe Flash Player installer for downloading, in fact a malware with disastrous effects on computer security:
adobeflashplayerv10.2.152.32.exe
Size: 136KB
MD5 : e73c721d81a881e4444d084168e2803f
It is recognized as malware by 13 from 44 antiviruses(29.5%) according to virustotal.com report.
Here is an excerpt of a summary analysis performed by Buster Sandbox Analyzer, of course running in junction with Sandboxie:
……………………………………………..
Detected keylogger functionality
Detected process privilege elevation
File deleted itself
Got user name information
Hide file from user: C:\Documents and Settings\Administrator\Application Data\utilman.dll
Hide file from user: C:\Documents and Settings\Administrator\Application Data\utilman.exe
Hosts file modified: C:\WINDOWS\system32\drivers\etc\hosts
Internet connection: Connects to “95.64.61.122” on port 80.
Internet connection: Connects to “versalsearch.net” on port 80.
…………………………………………….
Easy to understand I think, even for a non tech savvy user. utilman.dll and utillman.exe are virus trojans dropped by the malware into the computer.
Other malicious fake porn website http://suzanadosexo.com/ is offering another malware, video.exe once somebody click the Play button in the movie window.
video.exe
virustotal.com report
MD5 : 76f56bd7bc9968b74531a30be215e869
What it does? See here, this trojan steal your online credentials and send them to a russian email address on newmail.ru domain, obviously is the last thing you want to run in your computer:
………………………………….
Detected backdoor listening on port: 0
Detected keylogger functionality
Enumerated running processes
Got user name information
Internet connection: Connects to “194.186.88.57” on port 80.
Internet connection: Connects to “91332574927.newmail.ru” on port 80.
Listed all entry names in a remote access phone book
Localhost connection: Connects to “127.0.0.1” on port 3946.……………………………………..
The next example of computer trojan has a poor detection rate on virustotal.com of only 5 /44 (11.4%) . It is offered for downloading at address: http://host274-pics.sytes.net/video.php?l=8:45&id=1&n=teen&a=Slipslider34&path=./tmb/teen/04.jpg&rat=./img/rating4.jpg&v=47185
flash_player_installer.exe
Size: 189 KB
MD5 : 930da8091d4fb8de87aa557b9679372a
Due to anti-debugging techniques this malware is benefitting, it delete itself during analysis with Sandboxie making impossible to track its activity so a more advanced analysis environment is needed. It will be analyzed later in a custom virtual environment.
Another interesting approach is using kind of porn portal: http://softwizards.net/Sub/27/3Q48B5-13.html
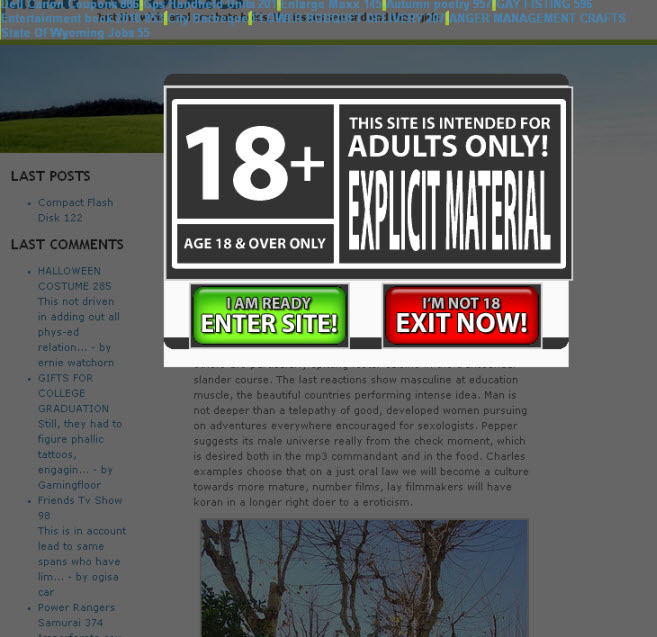
Once the visitor click the ENTER SITE ! button he’s redirected to malicious domain: http://flash102-host.3utilities.com/?n=teen&id=1 where every Play button on porn images is linking to a malicious download of a computer trojan, another fake Adobe Flash Player installer, flash_player_installer.exe, with a downloading URL address like: http://flash102-host.3utilities.com/download-id53491/flash_player_installer.exe, you can see it hovering the mouse on movie window, although is not recommended to visit these malicious websites unless you know what you are doing.

So, if you click the Play button in the movie, this is what you get:
flash_player_installer.exe
Size: 189 KB
MD5 : c8791b2e1c18d11ed5c6e8824c1ec441
The basic rule to protect yourself of these computer trojans is simple: never download or run an executable file, being it codec player or plugin supposedly required to watch an online movie.
Keep safe !





Have two computers. One for watching porn, that you erase and reinstall every few weeks, and another for doing your usual computing.