The common way to protect against network threats is installing a Firewall, which theoretically will block all attempting to establish a malicious connection, protecting the computer. It is well-known fact that always first step a hacker do trying to hack a computer in a network is a port scanning to find what ports are open and can be used to “communicate” with the target computer. Ports are in range from 0 to 65535, and some of them are assigned for special use as :
File Transfer Protocol(FTP) connections — port 21
Telnet — port 23
Hypertext Transfer Protocol(HTTP) — ports 80 and 81
HTTP over Transport Layer Security — port 443
and so on, the complete list can be found at www.iana.org
A site for testing common ports on your computer to find if them are vulnerable–open ports are www.hackerwatch.org , this site will do a ports scanning to your computer and warning you about the system flaws can prevent a future computer infection. The same can does a hacker, to find out which TCP and UDP ports are open and listening, which reveals to the hacker what services the system is offering over the network. For example the port used for file( or printers) shares is TCP port 445 assigned to Microsoft-DS Service and was exploited massively by worms(Sasser) and trojans. Once connected to this service, a hacker can download, upload or edit the shared files. Another ports very interesting from the hackers point of view are TCP and UDP from 135 through 139 associated to Microsoft file sharing SMB–a network file sharing protocol. If the hacker find an open port, he will try to find further what software is running and what exploitable vulnerabilities if any offer that software.
A firewall(software or hardware based) can prevent computer infections mainly by filtering data packets passed through the network device, and blocking those not matching the rules specified by the user or some security criteria. The firewall can be used also to open or block the user-specified ports.
In parallel with firewalls development, the virus programmers discover new methods to bypass the firewalls, techniques used in some RATs(Remote Administration Tool) popular known as trojans. Injecting a dll(the trojan was compiled as a dll) in the web browser known as fwb method(firewall bypass) was one of them. When firewalls was detecting the dll injection by implementing kernel API hooks, a new method called fwb+ was used. Using this method, the RAT can unhook or avoid the kernel and user level API hooks using sometimes a pe-loader for dll injection to avoid the detection. There is a more advanced method called fwb++. Reverse connection also is a lot used in trojans for bypassing the firewalls or NAT routers, it can establish a connection from inside the infected computer by opening a specified port and sending SYN packets. Assuming that usually a firewall does not block the outgoing traffic and the trojan(RAT) is injected in the browser process(or Explorer process but any other legitimate host process as Instant Messengers can be used), it looks to be a legitimate request so the firewall does not block the traffic. The hacker listens for these SYN packets and accept the connection, sending after that malicious commands to the RAT. Several Port Listeners can be used to prevent these malicious connections :
–Port Listener v1.01 is able to listen on multiple ports, while the data view allow us to analyze the data transfered;
–Port Listener XP can open fake ports confusing the hacker and logs the computer IP used to scan these fake ports and has nice features like :
– Multi-ranged ports for listening on.
– Easy to use GUI.
– Send Custom Data Back on connect.
– Enable on Startup.
– Msgbox alerts plus color coded warnings.
– Systray hiding options.
–Active Ports monitor all open ports and display the processes that open these ports. Also the local and remote IP address for each connection are revealed;
-Attacker by Foundstone.com, now a subsidiary of McAfee. It resides in the tray bar giving an alert each time it detects a connection attempt on any port.However it listens only to the incoming traffic and not to outgoing traffic.
As port scanners can be enumerated :
-Nmap, it’s a very effective and free tool for network monitoring. It’s able to scan large networks aswell as single hosts. A GUI–Zenmap is also available for who don’t want to use the classic command-line.
–Advanced Port Scanner it’s a fast and free port scanner for Windows 32 bits;
–Free Port Scanner 2.8.1 fast and robust port scanner for Windows all versions 32 bits;
–B&W Port Scanner 4.0 also a freeware;
A nice online utility for security auditing is : https://www.grc.com/x/ne.dll?bh0bkyd2;
as online port scanners can be found a lot, this is one of them: Port Scanner
The security for small and medium networks must be approached a little different. Instead of a firewall, recomandable for single hosts, more complex systems are used as Intrusion Detection System shortly IDS. The IDS monitor the traffic between hosts inside a network, and when it detects something suspicious using the heuristic or signature based method it trigger an alert received by the network Administrator. He will be warned aswell when an anomaly of the network traffic is detected.
Snort is the most known open source IDS and IPS where IPS stands for Intrusion Prevention System. It’s a command-line utility but a GUI is available.
An IDS from Sourcefire can be found here.
Another method used to prevent the computer infections from inside a network is using an Honeypot, kind of “hacking the hacker”. This method consists in setting up a false host system, false services or false valuable data inside the network, which will attract the hackers attacks like honey attract the flies. the system is totally isolated from the real network which will not be harmed in any way and while the intruder is busy trying to abuse the false host, all his actions are monitored and logged. Dealing with a such system, it’s a real headache for the intruder, wasting his time and patience with nulled actions and illusions. Using the Honeypot as an open proxy or an open relay for emails, will identify many spam sources, since the open proxies and open relays are heavily used by spammers. The Honeypot system behaviour and feedback is identically with the one of an abusable system making the spammers happy for a moment, but in the reality the real IP who generate the spam will be logged and spam will be blocked. A network containing more honeypots is called a Honeynet. For a better understanding of what is happening I’ve uploaded an image :
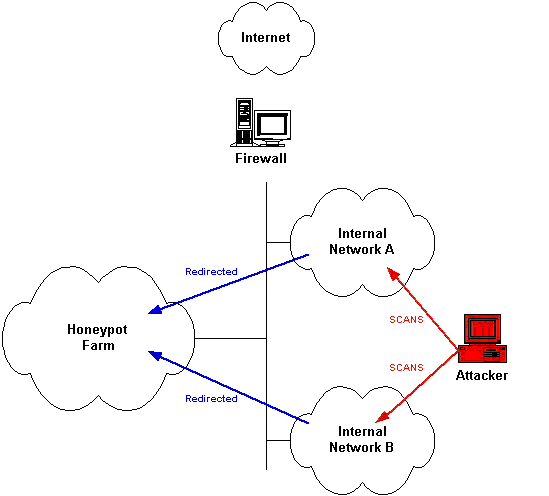
honeypot
A free HoneyBOT and also an interesting and more in deep reading about Honeypots can be found here, and another one is Google Hack Honeypot, written in PHP and assists the development of web-based honeypots.
There is also Honeypots detectors like Send-Safe Honeypot Hunter, which claims it can detect if an open proxy is a Honeypot or not.
Here must be said there is a lot of solutions used by hackers or Botnet creators to detect, disable or ignore the Honeypot systems by analyzing the initial traffic sent by the Honeypot. Here is an article about Honeypots limitations, ScienceDaily.
However, the biggest vulnerability in a network is the human factor. As long as corporations employees are logging in Social Networks as Facebook or Twitter sometimes from the offices they are working in, and gives confidential details to any sexy babe they meet, the entire corporation network is exposed to a big risk.





This is a nice post. I´ve encountered this article several times this week searching for something alike. Now is in my mail box 🙂 Keep up the good work!