A few days ago, I’ve noticed a new process applicationupdater.exe in the Task Manager processes list, but I did not pay too much attention to it, until today when I decided to discover what application is responsible for it. I mean, it’s normal for almost any application to connect to the web and update itself but respecting a few basic rules :
- the user must be asked previously for his consent to update a program
- an updater it’s not running for long, it runs at certain intervals, check the official site for updates and immediatelyit’s closing
- an application updater inform the user about what updates it’s looking for, for what program and if there is any updates available or not
At a certain moment, I realized that applicationupdater.exe an always-running process, which firstly I supposed to be what its name describes to be, has not a normal behaviour for an updater.
A short search on Google.com for this process reveal the fact this process is more than a mysterious one, it’s a possible threat, so I start to analyze it more carefull. The majority of the sites on the web sustain this application is installed in the computer via PDF Forge or PDF Creator programs, but I have none of these programs installed in my computer or at least downloaded, that’s mean the application was arrived and installed in my computer in other way, I simply don’t know how, I very often download trials or open source programs for testing purposes.
First of all, the program create a Windows service (that’s why it runs continuosly) with name :
Application Updater
and a vague description:
Automatically downloads and installs application updates
This does not sound good, it does not make any reference to any application which is supposed to be updated.
The installation path is :
%Program Files%\Application Updater\applicationupdater.exe
and from the file Properties :
- Company: Spigot, Inc
- File version: 1.1.2.16
- Original File name: ApplicationUpdater.exe
Further more, the analysis is made with Sandboxie 3.46 with Buster Sandbox Analyzer(BSA) add-on. The following actions are reported by the Malware Analyzer module :
- Defined Autostart registry location added
- Detected keylogger functionality
- Enumerated running processes
- Internet connection: Connects to “.mybrowserbar.com” on port 80.
- Listed all entry names in a remote access phone book
- Opened a service named: RASMAN
- Opened a service named: Sens
Risk evaluation result: High
The full report :
[ General information ]
* File name: c:\documents and settings\administrator\desktop\tests\applicationupdater.exe
* File length: 380928 bytes
* File signature: Microsoft Visual C++ ?.? *
* MD5 hash: 293e66aa529f0fba1aa56340e293a389
* SHA1 hash: 48ce7f1e56dbfc352c67e8081b4381f4e6826b2f
* SHA256 hash: bb9a50948b0fe28011566a1d36c4e9b6485bac0d1e95eb2ded0b82422f495a81[ Changes to filesystem ]
* No changes[ Changes to registry ]
* Deletes Registry key HKEY_LOCAL_MACHINE\software\Classes\clsid\{E7E6F031-17CE-4C07-BC86-EABFE594F69C}
* Creates Registry key HKEY_LOCAL_MACHINE\Subscriptions
* Creates value “SBIE_ProcessId=EC050000” in key HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Application Updater
* Creates value “SBIE_CurrentState=04000000” in key HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Application Updater
* Creates value “SBIE_ControlsAccepted=01000000” in key HKEY_LOCAL_MACHINE\system\CurrentControlSet\Services\Application Updater
* Modifies value “SavedLegacySettings=46000000280A0000010000000000000000000000000000000400000000000000C0C2EB74--0031CB0101000000C0A80165000000000000000000000000” in key HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
old value “SavedLegacySettings=46000000270A0000010000000000000000000000000000000400000000000000C0C2EB74--0031CB0101000000C0A80165000000000000000000000000”
* Deletes Registry key HKEY_CURRENT_USER\software\classes\*\shell\sandbox[ Network services ]
* Looks for an Internet connection.
* Connects to “.mybrowserbar.com” on port 80.[ Process/window information ]
* Keylogger functionality.
* Creates a mutex “CTF.LBES.MutexDefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Creates a mutex “CTF.Compart.MutexDefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Creates a mutex “CTF.Asm.MutexDefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Creates a mutex “CTF.Layouts.MutexDefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Creates a mutex “CTF.TMD.MutexDefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Creates a mutex “CTF.TimListCache.FMPDefaultS-1-5-21-839522115-261903793-1417001333-500MUTEX.DefaultS-1-5-21-839522115-261903793-1417001333-500”.
* Enumerates running processes.
* Creates a mutex “AppUpdaterPingMutex_BF46BBD8-8935-4adf-B837-19951E6E4AEC”.
* Creates a mutex “Local\_!MSFTHISTORY!_”.
* Creates a mutex “Local\c:!documents and settings!administrator!local settings!temporary internet files!content.ie5!”.
* Creates a mutex “Local\c:!documents and settings!administrator!cookies!”.
* Creates a mutex “Local\c:!documents and settings!administrator!local settings!history!history.ie5!”.
* Creates a mutex “RasPbFile”.
* Lists all entry names in a remote access phone book.
* Opens a service named “RASMAN”.
* Opens a service named “Sens”.
The analysis continues with Process hacker , and ApplicationUpdater service is seen connecting to :
174.36.215.20-static.reverse.softlayer.com remote port 80, local port 1227 and 1226 TCP
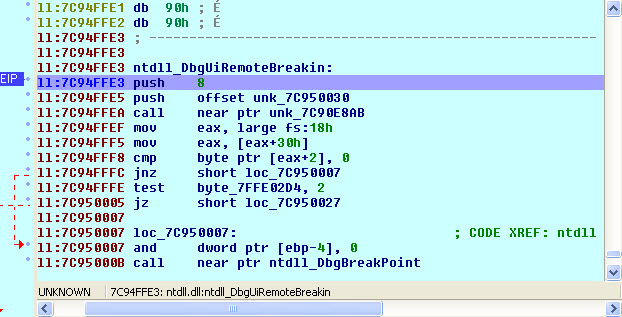
Perhaps an interesting fact is observed using a debugger like IDA – The Interactive Disassembler : applicationupdater.exe contain code to call a Windows function which prevent a debugger to be attached to the target process. A debugger, for who does not know, is a tool for examining a program code, running it instructions by instructions or step by step controlled by the user, attaching itself to the target process. This way, the program flow can be better understood and an eventually bug can be track down. However, using some Windows functions or other tricks, a program can “verify” if it’s debugged and prevent the debugger running normally, forcing the termination of the process immediately.
applicationupdater.exe uses functions like ntdll!DbgUiRemoteBreakIn or ntdll!DbgBreakPoint in order to avoid a debugging session.
It must be mentioned that under the run key of the registry-the main AutoStart registry key, a new value is created for an Internet Explorer BHO (Browser Helper Object) a dll with name “searchsettings.dll” by the same company Spigot, Inc. The complete object path is : c:\program files\search settings\searchsettings.dll and the folder contain also an executable, “searchsettings.exe”.
It can be observed a be behavioral change of both browsers used by me, Firefox 3.6.10 and Internet Explorer 8, the startup page URL adress is something like :
http://search.conduit.com/ctid=CT2475029&SearchSource=13
and the browser windows is displaying a search box similar to that of Google.com but with a banner to a well known software vendor.
Considering all these, it’s obvious that applicationupdater it’s an agressive and dangerous advertising tool which is affecting the user privacy and worsening the user Internet experience. Hiding its scope and its actions from the user, it is a constant threat to the safety of the computer system and my recomandation is to get rid of it as soon as possible.
Keep safe !





Thanks a lot for the explanations! PDF Creator did install this without my consent and Firefox started to behave strangely. Now it’s fixed :manual deletion of the folder and a scan with Malwarebytes’ Anti-Malware to prevent system restore etc.
Thanks a lot for a very professional and thorough analysis!
Nice article, let’s see if it works for me…
Thanks a lot for taking time to share you knowledge with the internet community.
On one of my systems AVG 2011 Internet Security recently alarmed me of the “applicationupdater.exe”, which made me search the web for some help – and again, I really appreciate your efforts.
Based on your input I’ll let AVG remove this program.
Hello thank you for this explanation. I also have the ‘Application Updater’ situation and was advised by AVG. I also have PDF Creator installed.
I have attempted to remove the program through the Uninstall Programs option (the computer does not see the file) and manually – whereupon the computer tells me that I do not have permission to uninstall the file. On further exploration, it appears that there is NO administrator on my computer (how is that possible?) I have two user accounts, both for me, both supposedly being labelled as ‘administrator’ accounts but neither have permissions to do anything that an administrator would do. I also have a guest user, which has no permissions.
The administrator issue may be a red herring here – but without one, I can’t remove the .exe however I have successfully removed (manually) the subsidiary file within the folder.
It’s interesting that today (Sat 28 May 2011) is the first time AVG has thrown this warning issue up (the warning was for pdfforgeToolbar.exe which AVG could not find nor move to vault and the ‘go to file’ option went somewhere else entirely)
The PDF Creator was installed in February 2011 and apparently the Application Updater.exe was installed at the same time.
Thanks if anyone can show me how to get this sorted. I’ll keep the page open till mid-june.
Regards
Berry
Hey Berry….I faced the same problem…If you have a parallel version of Linux you can log on to that and remove the file or just start windows in safe mode with command prompt and remove the file with the del command(go to the directory and type del ApplicationUpdater.exe”)…I have Norton 360 installed and it did not even recognize it as a threat when I ran Insight Scan….does anybody have any idea how to reverse the registry changes??
To get rid of the service you can open a command prompt that has Admin Authority and type:
sc delete “application updater”
with the quotes. This removes the service from the registry and will prevent you from getting errors in Event Viewer about the service not able to start.
great article; whell, that’s why antiviruses are useless! .
I am using also Pdf creator for a long time and I am very pleased of the program.
Also i have recently installed version 0.9.7 of the software with the browser toolbar component.
I think that this toolbar it is very useful to search anything, on yahoo, ebay and amazon.
It gives the opportunity to connect to ebay website automaticall that from my point of view is very good because I am an ebay client.
Having less free time, this toolbar is giving me the opportunity to quickly access ebay, amazon and to seek necessary information on yahoo search.
Like other search toolbars, web page image results are visable in a search tray for easy review of not only the visual images of the site but also the written headlines.
This is not spyware or adware.
Searching through other threads I found these links that I think can help everyone
http://www.spigot.com/uninstall.html
http://www.spigot.com/network_error_assistant.html
I noticed the same problems as e1 else, IE slowed a bit, acts strange at times, and applactionupdater always running.
But I don’t have and never did have PDF Creator. I did track it down though to another toolbar, YouTube Downloader Toolbar v4.5.
As a matter of fact a check says I accessed the program just a few mineuts ago, but I never enabled the toolbar since I installed the YouTube Downloader program. So yes it is quietly working in the background. Oh I I only opened the program once back on the day I installed it. Heres what My IE says….
Name YouTube Downloader Toolbar
Publisher Spigot, Inc.
Status Disabled
Type Toolbar
Last accessed ?Today, ?July ?19, ?2011, ??9 minutes ago
File date ?Friday, ?June ?24, ?2011, ??6:22 PM
File youtubedownloaderToolbarIE.dll
In folder C:\Program Files\YouTube Downloader Toolbar\IE\4.5
Load time (0.00 s)
Navigation time (0.00 s)
And…
Name YouTube Downloader Toolbar
Publisher Spigot, Inc.
Status Disabled
Type Browser Helper Object
Last accessed ?Today, ?July ?19, ?2011, ??9 minutes ago
File date ?Friday, ?June ?24, ?2011, ??6:22 PM
File youtubedownloaderToolbarIE.dll
In folder C:\Program Files\YouTube Downloader Toolbar\IE\4.5
Load time (0.00 s)
Navigation time (0.00 s)
As you see it says now that I accessed it 9 minutes ago, but I didn’t.
I’m gonna use Revo Uninstaller on it and do a “Forced Uninstall” and left over program/regestery files.
and see if that gets rid of this problem program. Also I’m gonna send all this to Nortons and see what they say about it.
Ciao a tutti/e. Ciao John
Grazie per l’articolo, molto esplicativo, anche se non l’ho capito tutto: non ne ho le competenze necessarie!
Vorrei sottoporti un quesito: se cancello il file “applicationUpdater.exe” (della Spigot) i programmi “Pdf Creator” e “Pdf Forge Toolbar” continueranno a funzionare normalmente? Li uso da tempo e mi sono molto utili, non vorrei rinunciarci. Se la risposta è scontata mi scuserai: non sono un tecnico. Grazie.
Silvio
Nice job.
Mine came along with a “youtube downloader” install.
Yes, PDF Creator is functioning even after applicationupdater.exe deletion
I manually deleted Application Updater using Advanced System Care 4 “Shredder” component. It deleted it but I still get the “Spigot Search Settings” window on boot up. Can’t find the folder for it on my system, can’t see it in Add/Remove Programs. Any help?
P.S. crisulici, you are an ass for going around to all the sites that ask how to remove this piece of malware and saying it is a great piece of software that is sooooo useful and not a threat. If it were useful and not a threat I would be able to see it, find it, delete it and it would NOT download itself to my computer or anybody else’s. This is MALWARE plain and simple.
I used the windows search and removed spigot.exe and widgetoolbar..
revo uninstall, removed even more on other pc,i think it’s dangerous and mean of youtubedownloader.
lol…i have the same kind of annoying malware/spware ..or whatever it is,,,,,,,,,,,searchsettings.exe , youtube downloder IE.exe and …applicationupdater…these three were running in mah process………its EASY to delete them without using any soft. or antivirus crap…run in safe mode..go to regedit.exe and just delete the registry entries..these fukin malware will dissapear for good….but m not sure if they r fully gone
Thanks, nice analysis comprehensive I mean
HI,
I had questioned this for about a week now. After intalling IOrbit software it appeared and after researching this it is part of the IORBIT Toolbar software. It can be uninstalled eaisly however, if you have iorbit toolbar, it may not provide good security within your toolbar. I have monitored this with Bulldog Antivirus and with the best malware software from CNET and it shows as safe. I’m always concerned as anyone would be when you have any connection protocal running without any explanation. I’m sure the Spigot company is the vendor for Iorbit toolbar and provides the tcpip security. So far I have had no problems at all, other then a concern to where this came from.
I hope this helps.
Safe Surfing,
Chase Michaels
Hi, my name is Laurentiu and I work for Spigot.
To remove ApplicationUpdater.exe please take a look here: http://www.spigot.com/remove-application-updater.html
Please contact me from our website http://www.spigot.com/contact.html if you need more help.
Thank you.
Hello – I ought to say, I’rm impressed along with your internet site. I had no trouble navigating by way of all the tabs and details was very straightforward to access. I found what I wanted in no time at all. Pretty awesome. Would appreciate it in the event you add forums or something, it would be a perfect way for your clients to interact. Fantastic job
check this bho.dll download post to know more details about Browser Helper Object….