These days we assist at a worldwide growing threat, the Ransom Trojan(named so by Kaspersky, and Winlock by Dr.web) which is a quite large family. The behaviour of this kind of computer trojan is different from variant to variant but as a general rule they blocks the files and folders access and demand money to restore the normal functionality. The victims are blocked out of the computer, the keyboard and the mouse are partially disabled and a message window appears announcing basically that the computer is blocked and the victim must send the payment to receive the unblock code via SMS at certain phone numbers. That’s it, the computer is hijacked and the attackers demand money to restore it. Why I said the keyboard is partially disabled ? Because it can be used only to introduce the presumably received code in the code box of the unlock window. Considering the language used in these threatening messages, it seems the main source of these trojans is the russian space.
Very often a countdown is displayed in the message window meant to urge the victims to send the payment and various threats are displayed scaring the users with files and folders permanent deletion or even Windows and BIOS (!!!) deletion if they do not pay for onlock code. Of course the BIOS which is stored in a ROM chip can not be deleted by a software being it even a strong virus.
There are variants of Ransom Trojans or cryptoviruses which encrypt the documents(.doc, .html, .jpg, .xls and so on) it finds in an infected computer for good(as example PGP Coder the newest variant uses RSA-1024 and AES-256 encryption algorithms, impossible to break and recover files, the only solution being to buy a decoder from the attackers) while other ransomware trojans are designed only try to scare the victims.
There are various ways to spread ransom trojans as in email attachments, free software offers and the most actual one is as a porno video codec or porno video player.
A particular case is porno-rolikXX.avi.exe, a fake porno video player spreaded by a few russian porno websites.
http://girlcoolfucking.info/1/video/porno-rolik1.avi.exe
http://pornositerufree.ru/11/video/porno-rolik11.avi.exe
http://pornositerufree.ru/12/video/porno-rolik12.avi.exehttp://shkollnitsiebutsya.ru/16/video/porno-rolik16.avi.exe
http://shkollnitsiebutsya.ru/17/video/porno-rolik17.avi.exehttp://mamkidayutvpopku.ru/17/video/porno-rolik17.avi.exe
http://mamkidayutvpopku.ru/18/video/porno-rolik18.avi.exe
The variants are repacked and differ each from other as file properties(Size, File Description, Copyright information) making harder the antivirus detection using the MD5 hash or file signature. On the other side, the authorities push offline very quickly these kind of sites but they continue to appear on new registered malicious domains.
For example porno-rolik11.avi.exe has a low detection rate of 41,9% according to virustotal.com – only 18/43 antivirus software detect it. Immediately after computer infection with this trojan a reboot is initiated and a message window is presented to the user:
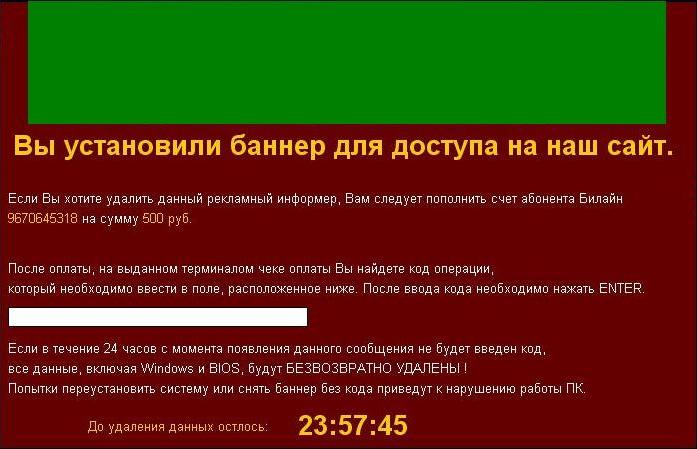
The green zone of the window is fulfilled with porno images. At this moment the computer mouse is locked and the keyboard can be used only to introduce the unlock code in this window. Strange enough Ctrl-Alt-Del combination to run the Task Manager is working but the keyboard arrows to select the malicious process and kill it are disabled. When the infection occurs, the trojan file is deleted from its original location and the trojan file is saved with a random name consisting from numbers(897911178.exe in this example) in:
Documents and Settings\%username%\ folder for Windows XP
Users\$USER$\ folder for Windows Vista and Windows 7
This ransom trojan assures its autorun by writing a value(in this case it was: “897911178=C:\Documents and Settings\Administrator\897911178.exe”) in the registry under Run key :
HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Run
To initiate a forced computer reboot, the trojan enables the SeShutdownPrivilege and SeRemoteShutdownPrivilege and the command is :
C:\WINDOWS\system32\shutdown.exe” /r /f /t 3
The trojan writes a value “NukeOnDelete=00000001” in registry key:
HKEY_LOCAL_MACHINE\software\microsoft\Windows\CurrentVersion\Explorer\BitBucket
This registry entry bypass the Recycle Bin in the case in which files or folders are deleted – they would be permanently deleted and will not go first to Recycle Bin. Of course the files can be recovered with a file recovery program as long as them are not overwritten. This can be an indication that the virus creator is not joking when he threatened that his trojan will delete some files from the system when the count down ends.
It is interesting a value that this ransom trojan add in key HKEY_CURRENT_USER\software\classes:
“SymbolicLinkValue=5C00520045004700490053005400520059005C0055005300450052005C00530061006E
00640062006F0078005F00410064006D0069006E006900730074007200610074006F0072005F004400650
06600610075006C00740042006F0078005C0075007300650072005C00630075007200720065006E007400
5F0063006C0061007300730065007300”
SymbolicLinkValue is a special registry key of type REG_LINK not well documented by Microsoft. It is a registry key which links or points to another registry key in a so called symbolic link mechanism. The value is supposed to be an Unicode string and does not need to pass any length validation when it is set, this being considered a vulnerability of Windows XP kernel which makes in this case unsafe assumptions about the registry values. An Unicode character must be 2 bytes long but we can set a 5 bytes long string as SymbolicLinkValue and reference it, this can lead to an unexpected behaviour of an Windows XP machine, even to crash it.
This vulnerability was well covered in an Hispasec paper written by Matthew “j00ru” Jurczyk and Gynvael Coldwind and the symbolic link mechanism was better described here than on Microsoft site. Microsoft reference this vulnerability as CVE-2010-0235 in Microsoft Security Bulletin MS10-021. Registry links represents an enormous potential for virus creators allowing them to manipulate the registry at their willing unnoticed or to deceive the antivirus detection which is monitoring some of the sensible registry keys.
Back to the subject, decoding the above SymbolicLinkValue results this:
REGISTRY\USER\Sandbox_Administrator_DefaultBox\user\current_classes
which is a kernel-mode representation of HKEY_USERS registry hive.
Sandbox_Administrator_DefaultBox is part of the string because this ransom trojan was ran and analyzed sandboxed.
Let’s imagine a hypothetical situation, what we can do if we get infected with a ransom trojan that bypass our security software?
DrWeb antivirus vendor has a free unlocker web page which offer unlock codes for a lot of ransom trojans. Kaspersky has also an unlocker here. At xylibox.blogspot.com website you can see a summary analysis of the “porno-rolik” trojan variants.
Other nice solutions to remove ransom trojans are available for more experienced users, they can simply delete the trojan file accessing the files from outside the Windows, using a Live Linux USB drive for example or better they can delete the registry entries made by the trojan once they know their locations.
It’s obvious that deleting the “run” value inserted by the trojan in HKEY_CURRENT_USER\software\Microsoft\Windows\CurrentVersion\Run key we can be sure the trojan will not run at the next computer start up.
Other registry key used for ransom trojans autostart is:
HKLM\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\Winlogon\userinit
userinit has initially a value of C:\WINDOWS\system32\userinit.exe and launch userinit.exe responsible for loading the user settings when the user is logging on. Adding another string at the value for example C:\WINDOWS\system32\userinit.exe , ABC.exe will launch also ABC.exe concomitently with userinit.exe
For editing registry from outside the Windows there is a free and nice utility called PC RegEdit it comes in .iso format ready to be burned on a CD which will be bootable. This utility provide a simple and clean solution to remove the autostart registry entries not only for the ransom trojans but for the viruses of all kind. After rebooting the computer, it’s far simpler to remove(delete) a virus file because it does not run, than fight against it when it has its own process or it is injected in another process as a protection strategy.
It’s recommended to use this utility to remove the trojans registry entries(and not the trojan file yet), boot again in Windows and see how our files and folders are looking: if they are very important documents and are encrypted, the only solution is to run the trojan again and pay for a decoder but if all is looking O.K., we can remove the ransom trojan executable file and forget it. However, the ransom trojans which truly encrypt the files are very rare, almost nonexistent these days, the most actual trojans try only to scare users in order to make a quick payment – this applies also to the porno-rolik trojans.
Because of method of spreading — via porno websites which receive a massive traffic, it can be expected a growing number of infected computers in the near future and not only from russian space — not only the russians love porno.
Keep safe !





I hope these Russian criminals get what they deserve i.e. facing a firing squad.
It’s great to read something that’s both enjoyable and provides pragmatisdc soluitnos.